How To Import Encryption Keys
BeepBackup uses GPG (GNU Privacy Guard) encryption to secure your backups:
- You provide us a public key: Upload your GPG public key to BeepBackup.
- Data is encrypted locally: Backup data is encrypted before sending it to your storage provider.
- Encrypted data goes to S3: The encrypted backups are stored in your S3 bucket, preventing your provider (and others) from reading it.
- You control decryption: Only you have the private key needed to decrypt your backups.
Prerequisites
You need the following things to follow this article along:
- A GPG key, which you can generate here if you don’t have one yet.
- An account at BeepBackup.
Importing Your Public Key
Importing your public key is not too difficult. After generating your key you can export the public key.
- First check which keys you have available with
gpg --list-secret-keys --keyid-format=long.
From the list of GPG keys, copy the long form of the GPG key ID you’d like to use. In this example, the GPG key ID is12345678ABCDEFGH:$ gpg --list-secret-keys --keyid-format=long /Users/beep/.gnupg/secring.gpg ------------------------------------ sec ed25519/12345678ABCDEFGH 2025-05-24 [expires: 2028-05-23] uid BeepBackup <info@beepbackup.com> ssb ed25519/XXXXXXXXXXXXXXXX 2025-05-24 Now that you’ve generated the key, and found the key id, you can use it to view your public key. Run gpg --armor --export 12345678ABCDEFGH to view the public key. - Next run
gpg --armor --export 12345678ABCDEFGH(replace12345678ABCDEFGHwith your key ID). - You now see your public key. Copy the full public key, starting from
-----BEGIN PGP PUBLIC KEY BLOCK-----and including-----END PGP PUBLIC KEY BLOCK-----at the end. - Navigate to the Encryption Keys page in BeepBackup. Click “New Encryption Key”.
- In the modal that opens up, paste in your public key. You can also give your key a recognizable name.
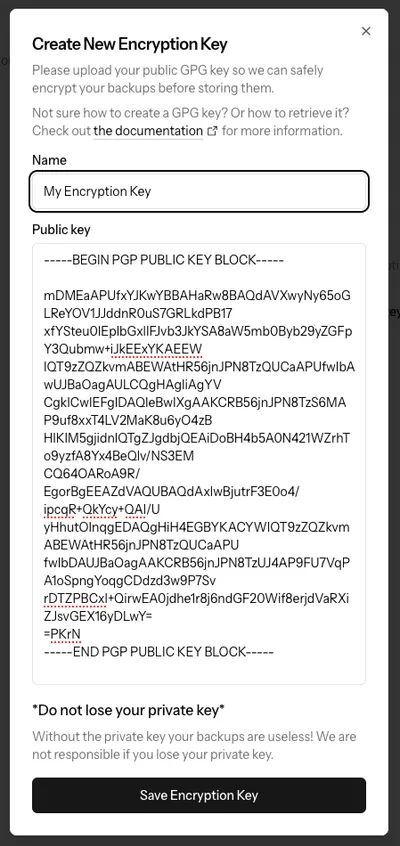 Click “Save Encryption Key”, and you’re all done!
Click “Save Encryption Key”, and you’re all done!
Good job. Now that you’ve added the encryption key, you can securely encrypt all your backups with it!
Next Steps
Now that you’ve added your encryption key, you can get started with configuring backups!